Next-Gen Cyber Security Solutions
Fortify Your Digital Perimeter with AI-Driven Security
Defend your enterprise infrastructure against evolving cyber threats through intelligent threat detection, autonomous incident response, and zero-trust security frameworks.
Cyber Shield Services
Augmented Protection & Strategic Risk Eradication
Defend your online framework through top-tier cyber defense solutions. From sophisticated hazard identification to total information integrity, we empower organizations to stay a stride forward of cyberthreats. Defend your online framework through top-tier cyber defense solutions. From sophisticated hazard identification to total information integrity.
Threat Prevention
Blocks cyber attacks before happening
Data Encryption
Protects sensitive business data
Risk Assessment
Identifies weaknesses in your defenses
Rapid Response
Rapid cyberthreat response
Unified Security Architecture
Complete Cyber Assurance & Strategic Resilience
Empower your organization with compact fortification and precision-driven security methodologies. From real-time threat diagnostics to post-incident analytics, we deploy scalable and intelligent defenses against the full spectrum of digital adversaries.

Prediction
Stay steps ahead of attackers with predictive threat modeling and AI-enhanced security analytics.

IoT Security
Secure every endpoint, including mobile and IoT devices, with our adaptive protection systems.

Deep Scanning
Uncover hidden risks with enterprise-grade scanning tools and comprehensive penetration testing.

Forensics & Analysis
Trace, dissect, and neutralize malware with advanced forensic tools and real-time response.

End-to-End Encryption
Protect data in transit and at rest with military-grade encryption protocols across your network.

Custom Architecture
Tailored cybersecurity frameworks built to scale with your business and evolving threats.

Threat Detection
Utilize machine learning to detect anomalous behaviors and thwart zero-day threats in real-time.

Compliance Monitoring
Maintain industry standards and certifications with always-on compliance automation.

What Distinguishes Daedalus Hub
Expertise Trusted Safeguards Support
At Daedalus Hub, we fuse domain intelligence with next-gen cybersecurity frameworks to proactively secure your digital ecosystem. Our customized methodologies driven by expert analysts and scalable architectures deliver resilient, adaptive, and forward-compatible protection for mission-critical assets.
Future-Proof Security
Intelligent Protection & Sustained Cyber Resilience
We reinforce every tier of your security architecture with intelligent, automated defense systems. From real-time vulnerability detection to actionable governance, our integrated approach amplifies visibility, strengthens control, and fortifies digital assets.

Compliance Alignment
Stay compliant with industry regulations effortlessly. Our solutions align with GDPR, ISO, and other standards.

Data Loss Prevention
Protect your sensitive information from leaks. We apply controls to keep proprietary data completely secure and safe.

User Access Control
Manage and limit who can view or modify resources. Our framework enforces policies for role-specific access.

Scalable Cloud Security
Safeguard workloads across multicloud platforms. We enable you to scale securely while minimizing risk and protecting operations.

Continuous Security Validation
Test your defenses regularly to stay a step ahead. Our team performs ongoing assessments to validate controls.

Business Continuity Support
Design plans to keep operations running during a crisis. We enable your business to quickly recover and respond.
Cyber Impact Chronicles
Validated Solutions & Quantifiable Outcomes
We present real-world deployments where our strategic cyber interventions delivered mission-critical outcomes. From neutralizing advanced persistent threats to reinforcing enterprise-wide security architectures, Daedalus Hub empowers organizations with measurable impact.
01. Phishing Attack Prevention
We neutralized a sophisticated phishing campaign by identifying suspicious emails and blocking delivery promptly. Our intervention kept sensitive credentials and operations completely safe.
02. Insider Threat Prevention
03. Cloud Security Transformation
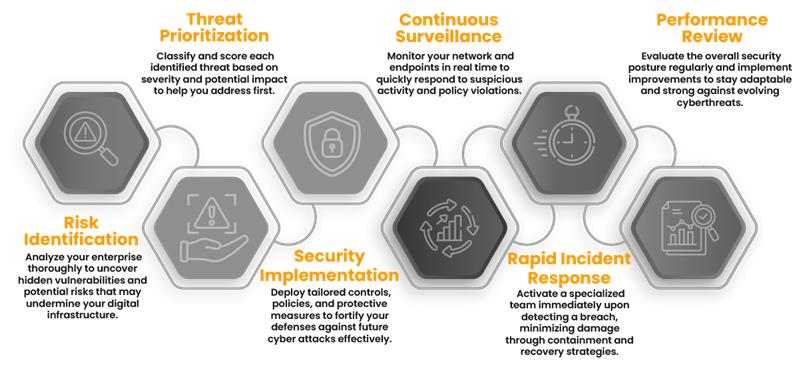
Cyber Defense Orchestration
Intelligent Cyber Security Workflow
At Daedalus Hub, we architect a seamless cybersecurity journey driven by automation, intelligence, and precision. Our structured flow from predictive exposure mapping to rapid incident neutralization enables full-spectrum protection, optimized response, and operational fortification.
Cybersecurity Insights
Frequently Asked Questions
Daedalus Hub guides businesses through their most pressing cybersecurity questions. With clear answers and actionable knowledge, we help organizations stay informed, adaptable, and resilient in a rapidly shifting digital world.
What is Daedalus Hub Cybersecurity?
Daedalus Hub Cybersecurity is a leading provider of enterprise security solutions. We specialize in protecting businesses from cyberthreats through advanced technologies, expertise, and a tailored approach to securing your digital ecosystem.
Why is Cybersecurity Important Today?
Cybersecurity safeguards your valuable data, operations, and reputation. As cyberthreats become more sophisticated, protecting your enterprise is a top priority to avoid financial losses and operational disruptions.
How Does Daedalus Hub Help Enterprises?
We provide a comprehensive suite of services, from vulnerability assessments to incident response. Our team collaborates closely with you to develop a robust, scalable, and adaptable cybersecurity strategy.
What Industries Do You Support?
Daedalus Hub serves businesses across sectors healthcare, finance, education, manufacturing, and more offering tailored solutions that match each industry’s unique risk profile and compliance requirements.
Are Your Solutions Cloud-Ready?
Yes. Our cybersecurity framework is designed to seamlessly integrate with multi-cloud and hybrid infrastructures, protecting your workloads and data no matter where they reside.
Do You Provide 24/7 Security Support?
We operate a Security Operations Center (SOC) around the clock. Our team monitors your network 24/7 and responds immediately to potential cyberthreats, minimizing risk and damage.
How Do You Handle Compliance Needs?
Daedalus Hub assists organizations in meeting industry and government regulations, from GDPR to ISO 27001. We align our controls to help you stay compliant and avoid penalties.
Will My Operations Be Disrupted?
We implement cybersecurity measures with minimal disruption to your daily operations. Our team plans and executes protective strategies to keep your business running smoothly and safely.
